Blog
The Blue Team Level One Certificate
As the sun sent its early morning light through my window, a sense of anticipation settled over me. This was not an ordinary day. It marked a significant moment in my journey through the world of cyber security. Resting within a small stack of mail was the physical proof of many hours of learning and practice. It was the Blue Team Level One certificate. Seeing it brought a feeling of pride and a wave of memories from the long and demanding twenty four hour incident response exam that it represented.
In this post, I would like to share not only the certificate itself but also the path that led to it. The Blue Team Level One certification represents more than a simple achievement. It is a meaningful stage in the growth of anyone who hopes to work as a defender in the cyber security field. It tests technical skills, endurance, and the ability to think clearly under pressure. Join me as I describe the experience of preparing for the demanding twenty four hour exam, the strategies that guided me through it, and the lessons that shaped my understanding of defensive security. Whether you already work in this field or are beginning to explore it, this story will offer insight into the process of earning this respected certification.
About the Blue Team Level One Certification
In the constantly changing world of cyber security, the Blue Team Level One certification has earned a strong reputation as an important qualification for junior security operations. Since its introduction in the year twenty twenty, it has become widely respected and has helped many defenders in many parts of the world. Professionals from government agencies, national response teams, law enforcement groups, military units, managed security providers, banks, and national infrastructure organizations all rely on the skills taught in this program.
A Panoramic View of Cyber Defense Skills
The Blue Team Level One curriculum guides learners through six important areas of defensive security. These areas are designed to help students build a complete understanding of how to defend digital environments.
- Security Fundamentals: A broad introduction that prepares students for advanced concepts.
- Phishing Analysis: Training to detect and understand phishing attempts.
- Threat Intelligence: Skills for studying and predicting hostile activity.
- Digital Forensics: Techniques used to extract and study digital evidence.
- Security Information and Event Management: Training in the use of platforms that monitor and analyze system events.
- Incident Response: Methods for acting quickly and effectively when a system is under threat.
Who Benefits from Blue Team Level One
The certification is suitable for anyone who wants to work as a defender of digital systems. Students develop skills such as:
- Identifying and stopping phishing attempts
- Performing detailed forensic analysis
- Using security platforms to study suspicious activity
- Reviewing logs and network traffic
- Researching threat actors
These are practical skills used by defenders around the world every day.
Why Blue Team Level One is Special
This program is helpful for:
- Students and information technology staff preparing for a career in security
- Security analysts seeking to deepen their understanding
- Responders who need to improve the speed and accuracy of their reaction to threats
- Analysts who focus on threat intelligence
- Specialists who study digital evidence
While the material is designed for early career or junior roles, it contains enough depth to challenge experienced professionals as well.
Recognition and Industry Alignment
The Blue Team Level One certification meets sixty percent of the one hundred twenty five requirements that appear in the National Initiative for Cyber Security Education guide for defensive analysts. It also meets sixty seven percent of the required knowledge and ability standards. This makes it a trusted and respected qualification within the cyber security community.
A Collection of Essential Tools
Students who complete the program gain experience with many important tools used throughout the world of cyber defense. Some examples include Autopsy, DeepBlueCLI, DomainTools, FTK Imager, KAPE, MISP, OpenCTI, PhishTool, PowerShell, Scalpel, Sigma, Snort, Splunk, Suricata, TheHive Five, VirusTotal, Volatility, Windows File Analyzer, and Wireshark. These tools support forensic study, threat investigation, incident response, and many forms of analysis.
About the Twenty Four Hour Incident Response Exam
The Blue Team Level One program includes a realistic and challenging exam that takes place within a cloud based laboratory. Students may begin this exam at any time within twelve months of purchasing the course. The exam contains twenty questions that require practical skill with tools, system analysis, and the study of hostile techniques based on the ATT and CK framework.
When the exam is completed, students receive their results immediately. A score of seventy percent earns the silver challenge coin. A score of ninety percent or higher on the first attempt earns the gold challenge coin. Students who do not reach the passing score receive a free retake voucher that remains valid for twelve months. This retake can be attempted after a waiting period of ten days. Additional retake vouchers may be purchased for one hundred pounds.
This twenty four hour exam is both a test of knowledge and an exercise in endurance. It is one of the most memorable steps in the journey of becoming a capable defender.
Preparing for the Twenty Four Hour Incident Response Exam
 The Blue Team Labs Online Platform
The Blue Team Labs Online Platform
My preparation for the exam relied on the Blue Team Labs Online platform. This is a practical and interactive learning environment that presents real security investigations and challenges. It includes scenarios in incident response, forensic investigation, security operations, reverse engineering, and threat hunting. The platform contains both free and paid levels, allowing many learners to take part regardless of budget.
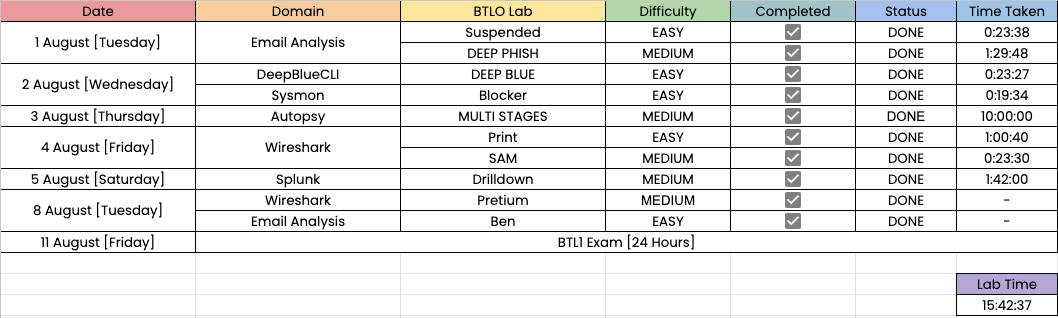 Time taken to complete each BTLO investigation
Time taken to complete each BTLO investigation
To build confidence before the exam, I completed ten investigation labs on the platform. These labs reflect the content of the six domains in the certification. They were not simple exercises. They were realistic situations that required careful thinking and precise action. The labs I completed were:
- Deep Blue
- Deep Phish
- Suspended
- Blocker
- Drilldown
- Ben
- Multi Stages
- Sam
- Pretium
Each investigation strengthened my understanding and sharpened my ability to respond to complex problems.
Attending the Twenty Four Hour Incident Response Exam
Approaching the twenty four hour exam requires both careful planning and strong discipline. The exam timer continues without pause, so it is important to create a strategy that includes periods of focused work as well as time for rest, meals, and short breaks. This helps maintain clarity and energy throughout the long session.
On the morning of the exam, I began at nine in the morning after breakfast. The exam unfolds through a detailed scenario, so the first step was to read the description carefully and understand the entire context. This preparation guided the way I approached the tasks that followed.
Although I had planned to use the full twenty four hours, I progressed more quickly than expected. I completed the main work by six in the evening and spent an additional hour reviewing my answers before submitting them.
Reflections and Lessons
The score I received was eighty percent. This meant that I answered sixteen of the twenty questions correctly and earned the silver challenge coin. There was a small sense of wondering what might have happened if I had been a little more precise, since two additional correct answers would have earned the gold coin. The feedback revealed that I had used an incorrect filter in Splunk, which resulted in two wrong answers. This was a helpful reminder of the importance of careful attention, even during long and tiring work.
 My Blue Team Level One Certificate and the Silver Challenge Coin
My Blue Team Level One Certificate and the Silver Challenge Coin
Looking back, the Blue Team Level One certification represents far more than a line on a resume. It marked a significant and meaningful stage in my cyber security journey. The experience encouraged me to continue learning. I am now preparing for the Certified SCADA Security Engineer certification with guidance from White Hat Hacker and the instructor known as OccupyTheWeb. I look forward to sharing more as this new chapter unfolds.